Updated EC-Council CEH 312-50v8 PDF & VCE Free Download Now (71-80)
QUESTION 71
_____________ is a type of symmetric-key encryption algorithm that transforms a fixed-length block of plaintext (unencrypted text) data into a block of ciphertext (encrypted text) data of the same length.
A. Stream Cipher
B. Block Cipher
C. Bit Cipher
D. Hash Cipher
Answer: B
QUESTION 72
Your company has blocked all the ports via external firewall and only allows port 80/443 to connect to the Internet. You want to use FTP to connect to some remote server on the Internet. How would you accomplish this?
A. Use HTTP Tunneling
B. Use Proxy Chaining
C. Use TOR Network
D. Use Reverse Chaining
Answer: A
QUESTION 73
You have successfully gained access to a victim’s computer using Windows 2003 Server SMB Vulnerability. Which command will you run to disable auditing from the cmd?
A. stoplog stoplog ?
B. EnterPol /nolog
C. EventViewer o service
D. auditpol.exe /disable
Answer: D
QUESTION 74
How do you defend against MAC attacks on a switch?
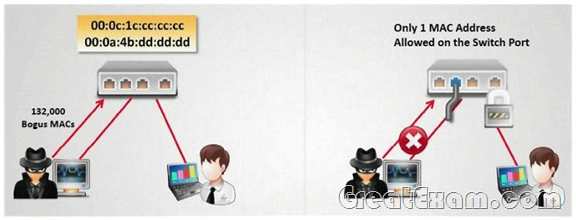
A. Disable SPAN port on the switch
B. Enable SNMP Trap on the switch
C. Configure IP security on the switch
D. Enable Port Security on the switch
Answer: D
QUESTION 75
In which location, SAM hash passwords are stored in Windows 7?
A. c:\windows\system32\config\SAM
B. c:\winnt\system32\machine\SAM
C. c:\windows\etc\drivers\SAM
D. c:\windows\config\etc\SAM
Answer: A
QUESTION 76
File extensions provide information regarding the underlying server technology. Attackers can use this information to search vulnerabilities and launch attacks. How would you disable file extensions in Apache servers?
A. Use disable-eXchange
B. Use mod_negotiation
C. Use Stop_Files
D. Use Lib_exchanges
Answer: B
QUESTION 77
Bob has a good understanding of cryptography, having worked with it for many years. Cryptography is used to secure data from specific threats, but it does not secure the application from coding errors. It can provide data privacy; integrity and enable strong authentication but it cannot mitigate programming errors. What is a good example of a programming error that Bob can use to explain to the management how encryption will not address all their security concerns?
A. Bob can explain that using a weak key management technique is a form of programming error
B. Bob can explain that using passwords to derive cryptographic keys is a form of a programming error
C. Bob can explain that a buffer overflow is an example of programming error and it is a common mistake
associated with poor programming technique
D. Bob can explain that a random number generator can be used to derive cryptographic keys but it uses
a weak seed value and this is a form of a programming error
Answer: A
QUESTION 78
Finding tools to run dictionary and brute forcing attacks against FTP and Web servers is an easy task for hackers. They use tools such as arhontus or brutus to break into remote servers.
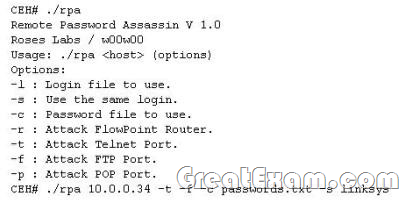
A command such as this, will attack a given 10.0.0.34 FTP and Telnet servers simultaneously with a list of passwords and a single login namE. linksys. Many FTP-specific password-guessing tools are also available from major security sites. What defensive measures will you take to protect your network from these attacks?
A. Never leave a default password
B. Never use a password that can be found in a dictionary
C. Never use a password related to your hobbies, pets, relatives, or date of birth.
D. Use a word that has more than 21 characters from a dictionary as the password
E. Never use a password related to the hostname, domain name, or anything else that can be found with whois
Answer: ABCE
QUESTION 79
One of the most common and the best way of cracking RSA encryption is to begin to derive the two prime numbers, which are used in the RSA PKI mathematical process. If the two numbers p and q are discovered through a _____________ process, then the private key can be derived.
A. Factorization
B. Prime Detection
C. Hashing
D. Brute-forcing
Answer: A
QUESTION 80
Data is sent over the network as clear text (unencrypted) when Basic Authentication is configured on Web Servers.
A. true
B. false
Answer: A
If you want to pass the EC-Council CEH 312-50v8 exam sucessfully, recommend to read latest EC-Council CEH 312-50v8 Exam Questions full version.