[January-2022]350-501 Dumps PDF Free Download in Braindump2go[Q172-Q201]
January/2022 Latest Braindump2go 350-501 Exam Dumps with PDF and VCE Free Updated Today! Following are some new updated 350-501 Real Exam Questions!
QUESTION 172
What are two characteristics of MPLS TE turrets? (Choose two)
A. They require EIGRP to be running in the core.
B. They use RSVP to provide bandwidth for the tunnel.
C. They are run over Ethernet cores only.
D. The headend and tailend routes of the tunnel must have a BGP relationship.
E. They are unidirectional.
Answer: BE
QUESTION 173
Refer to the exhibit. A network operator needs to shut down interface Gi0/0/0/2 for maintenance.
What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
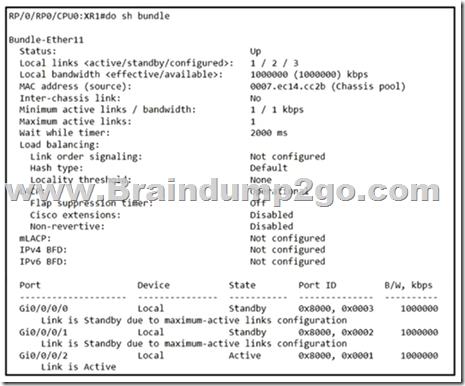
A. Gi0/0/0/1 and Gi0/0/0/0 become active
B. Gi0/0/0/1 and Gi0//0/0 remains standby
C. Gi0/0/0/0 becomes active. Gi0/00/1 remains standby
D. Gi0/0/0/1 becomes active Gi0/0/0/0 remains standby
Answer: D
Explanation:
The priority is 0x8000 an the lower Port ID wins.
https://www.cisco.com/c/en/us/td/docs/routers/xr12000/software/xr12k_r4-1/interfaces/command/reference/interfaces_cr41xr12k_chapter8.html#wp948389616
QUESTION 174
A customer requests that sites are connected over an MPLS backbone using the MPLS AToM service. However, the network engineer advises that the MPLS L3VPN service may be better for this situation.
Which characteristic of MPLS L3VPN may make it a better option from the Service Provider perspective?
A. Reduction of operational complexity.
B. Support for multiple network layer protocols, such as IP, IPX, and SNA
C. CustomerLayer 2 information will be maintained over the service provider core.
D. Transparent to the customer
Answer: A
QUESTION 175
An engineer needs to implement QOS mechanism on customer’s network as some applications going over the internet are slower than others. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two)
A. Configure a queue with sufficient memory to buffer excess packets.
B. Configure the token values in bytes.
C. Implement packet remarking for excess traffic.
D. Implement a scheduling function to handle delayed packets.
E. Configure a threshold over which excess packets are discarded.
Answer: AD
QUESTION 176
Refer to the exhibit. ASN 64501 currently reaches the networks under the 10.0.0.0/8 prefix via the North_B router, which is a slow backup link.
The administrator of ASN 64502 wants traffic from ASN 64501 to 10.0.0.0/8 to travel via the primary link North_A.
Which change to the network configuration accomplishes this task?
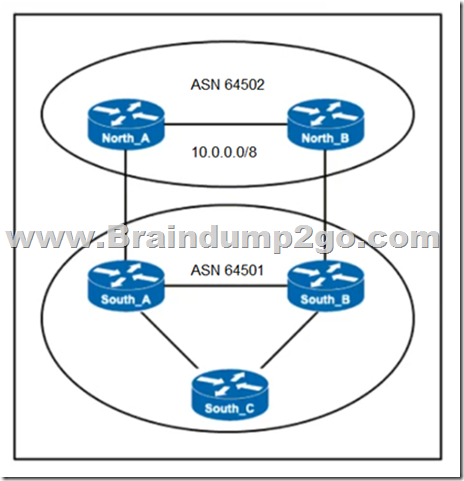
A. Set a higher local preference between North_A and South_A
B. Advertise the 10.0.0.0/8 prefix through North_B and specific subnets through North_A
C. Set a Lower Weight value for incoming traffic on North_A
D. Set a lower MED between North_B and South_B
Answer: B
QUESTION 177
A network engineer is configuring Flexible NetFlow and enters these commands.
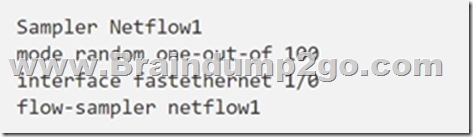
What are two results of implementing this feature instead of traditional NetFlow? (Choose two.)
A. CPU and memory utilization are reduced.
B. Only the flows of top 100 talkers are exported.
C. The data export flow is more secure
D. The number of packets to be analyzed are reduced.
E. The accuracy of the data to be analyzed is improved.
Answer: AD
QUESTION 179
Refer to me exhibit. A network operator recently configured BGP FlowSpec for me internal IT network.
What will be inferred from the configuration deployed on me network?
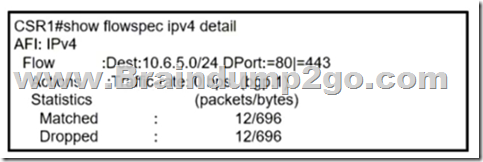
A. The policy is configured locally on CSRl and drops all traffic for TCP ports 80 and 443
B. The policy is learned via BGP FlowSpec and drops all traffic for TCP ports 80 and 443
C. The policy is warned via BC FlowSpec aid has active traffic
D. The policy is configured locally on CSR1 and currently has no active traffic
Answer: A
QUESTION 180
What are two factors to consider when implementing NSR High Availability on an MPLS PE router? (Choose two.)
A. It consumes more memory and CPU resources than NSF
B. It operates normally without NSR support on the PE peers.
C. It requires all PE-CE sessions to support NSR
D. It requires routing protocol extensions
E. It cannot sync state information across redundant RPs
Answer: AB
QUESTION 181
Which statement about TLS is accurate when using RESTCONF to write configurations on network devices’?
A. It requires certificates for authentication.
B. It is provided using NGINX acting as a proxy web server
C. It is used for HTTP and HTTPS requests.
D. It is not supported on Cisco devices
Answer: A
QUESTION 182
Refer to the exhibit. An engineer is updating this network to meet these conditions:
– Area 10 will receive inter-area routes and support mutual redistribution of external routes with the extranet.
– The ::/0 route is prohibited in Area 10.
– Area 11 will receive only the ::/0 route from the ABR.
– External route redistribution is not supported in Area 11.
– The ABR in Area 11 will advertise no interarea routes.
Which two configurations must be performed to meet the requirements? (Choose two.)
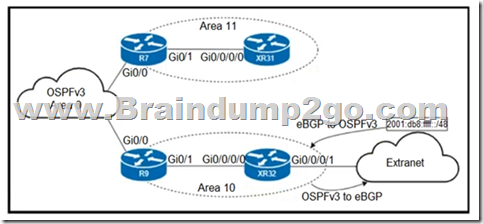
A. Configure area 11 as nssa no-summary on R7 and as nssa on XR31.
B. Configure area 10 as stub on R9 and XR32.
C. Configure area 11 as stub no-summary on R7 and as stub on XR31.
D. Configure area 11 as nssa default-information-originate on R7 and as nssa on XR31.
E. Configure area 10 as nssa on R9 and XR32.
Answer: CE
QUESTION 183
Refer to the exhibit. While troubleshooting a connectivity issue on router R2, a network engineer with an employee id:3876.13.497 notices that although it detects three OSPF links from R1, the OSPF prefixes are missing from the routing table. What is the reason for the problem?
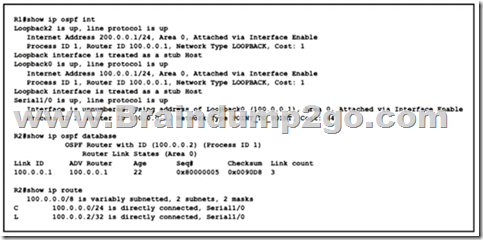
A. The serial interfaces have different MTUs
B. Both loopback interfaces on R1 are configured as stub
C. The R2 Serial 1/0 interface is configured with an IP address, but the R1 Serial R1 Serial 1/0 interface in unnumbered.
D. The subnet masks on the serial interfaces are mismatched.
Answer: C
QUESTION 184
What is the characteristic of the Tl-LFA?
A. It guarantees a loop-free path for all interfaces in the OSPf- super backbone.
B. It applies on each area and instance and makes all the interfaces inherit the configuration
C. It guarantees a loop-free path for all areas configured m OSPF
D. It applies only on the instance and makes at the interfaces inherit the configuration
Answer: D
QUESTION 185
Refer to the exhibit. A network engineer is deploying SNMP configuration on client’s routers. Encrypted authentication must be included on router 1 to provide security and protect message confidentially.
Which action should the engineer perform on the routers to accomplish this task?
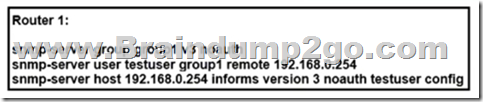
A. snmp-server host 192.168.0.254 informs version 3 auth testuser config.
B. snmp-server user testuser group 1 remote 192.168.0.254 v3 auth md5 testpassword
C. snmp-server group group 1 v3 auth.
D. snmp-server community public
Answer: B
QUESTION 186
The administrator of a small company network notices that intermittent network issues occasionally cause inbound notifications to its SNMP servers to be lost.
Which configuration must the administrator apply so that the SNMP servers acknowledge the notifications that they receive?
A. snmp-server community ciscotest rw 10
B. snmp-server host tests.cisco.com public
snmp-server community ciscotest rw 10
C. snmp-server enable traps bgp
snmp-server host 192.169.2.1 informs
D. snmp-server enable traps snmp
Answer: C
QUESTION 188
Which two actions describe ISP delegation to PCE servers? (Choose two)
A. adding a new PCE server with lower precedence than the primary PCE
B. changing the precedence of any of the PCE servers
C. removing TE re-optimization timer timeouts
D. entering the mpls traffic-eng reoptimize command
E. adding a new PCE server with higher precedence than the primary PCE
Answer: AE
QUESTION 189
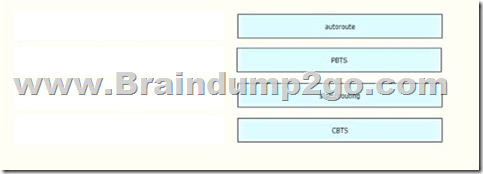
Drag and Drop Question
Drag and drop the methods of Cisco MPLS TE tunnel traffic assignment from the left onto their characteristics on the right.
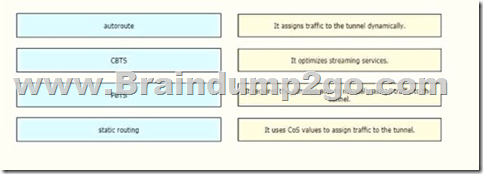
Answer:
QUESTION 190
Refer to the exhibit. An engineer needs to implement this QoS policy on customer’s network due to ongoing slow network issues.
What will be the effect on the network when the engineer implements this configuration?
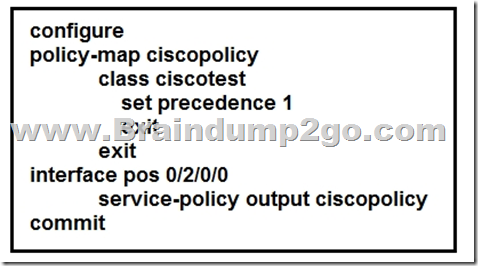
A. Traffic that is identified in the ciscotest class map will be remarked from IP precedence 1 to DSCP AF11 when it enters the pos0/2/0/0 interface.
B. Traffic that is identified in the ciscopolicy class map will be marked with IP precedence 1 when it enters the pos0/2/0/0 interface.
C. Traffic that is identified in the ciscopolicy class map will be remarked from IP precedence 1 to DSCP AF11 when it exits the pos0/2/0/0 interface.
D. Traffic that is identified in the ciscotest class map will be marked with IP precedence 1 when it exits the poso/2/0/0 interface.
Answer: D
QUESTION 191
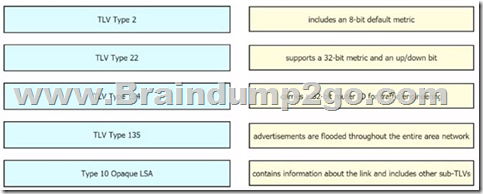
Drag and Drop Question
Drag and drop the descriptions from the left onto the corresponding OS types on the right.

Answer:

QUESTION 192
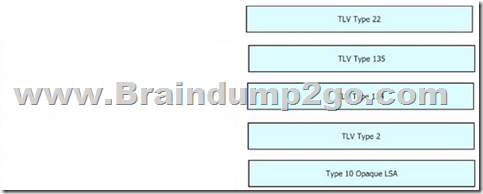
Drag and Drop Question
Drag and drop the OSPF and IS-IS Cisco MPLS TE extensions from the left to their functional descriptions on the right.
Answer:
QUESTION 193
A service provider is using QoS to manage customer traffic over the MPLS backbone.
Which three statements about the behavior of each MPLS QoS mode based on QoS policy in the service provider core are true? (Choose three.)
A. Uniform mode does not change the original CE IP packet markings.
B. Uniform mode changes the original CE IP packet markings.
C. Pipe mode does not change the original CE IP packet markings.
D. Pipe mode changes the original CE IP packet markings.
E. Short-pipe mode does not change the original CE IP packet markings.
F. Short-pipe mode changes the original CE IP packet markings.
Answer: BCE
QUESTION 194
A network engineer is tasked with supporting traffic discrimination over MPLS traffic engineering tunnels.
To allocate restricted bandwidth to a certain type of traffic with no QoS degradation, which technique must be used?
A. integrated services
B. MPLS TE Diff-Serv full allocation model
C. MPLS TE Diff-Serv Russian doll model
D. IP precedence
E. class of service
Answer: C
QUESTION 195
Which type of attack is a protocol attack?
A. HTTP flood
B. TFTP flood
C. SYN flood
D. Slowloris
Answer: C
QUESTION 196
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network.
Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
A. carriage of full Internet routes in a VPN. in the case of Internet access VPNs
B. Internet routing through global routing on a PE router
C. Internet access routing as another VPN in the ISP network
D. Internet access through leaking of Internet routes from the global table into the L3VPN VRF.
E. Internet access for global routing via a separate interface in a VRF
Answer: CE
QUESTION 197
Refer to the exhibit. To protect in-band management access to CPE-R7, an engineer wants to allow only SSH management and provisioning traffic from management network 192.168.0.0/16. Which infrastructure ACL change must be applied to router PE-R9 to complete this task?
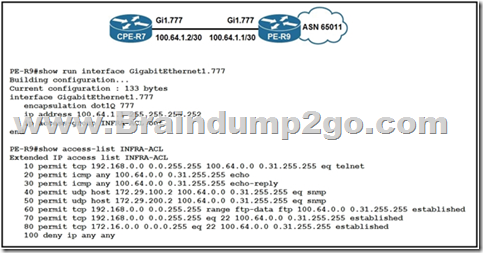
A. ip access-list extended INFRA-ACL
15 permit tcp 192.168.0.0 0.0.255.255 range 49152 65535 100.64.0.0 0.31.255.255 eq 443
B. ip access-list extended INFRA-ACL
no 10
15 permit tcp 192.168.0.0 0.0.255.255 range 49152 65535 100.64.0.0 0.31.255.255 eq 22
C. ip access-list extended INFRA-ACL
15 permit tcp 192.168.0.0 0.0.255.255 range 49152 65535 100.64.0.0 0.31.255.255 eq 22
D. ip access-list extended INFRA-ACL
no 10
15 permit tcp 192.168.0.0 0.0.255.255 eq 22 100.64.0.0 0.31.255.255 eq 22
Answer: B
QUESTION 198
An engineer implemented LDP protocol on the ISP network. The engineer must ensure that there are no packet loss issues when IGP and LDP protocols are not synchronized.
Which configuring must the engineer implement so that the IGP routing protocol will wait until LDP convergence is completed?
A. Disable IP CEF on routers running LDP and enable LDP protocol.
B. Configure MPLS LDP IGP synchronization on the network.
C. Configure LDP sessions protection on the network.
D. Disable MPLS LDP IGP synchronization on the network.
Answer: B
QUESTION 199
What is the function of the FEC filed within the OTN signal structure?
A. It allows the sending devices to apply QoS within the OTN forwarding structure.
B. It allows source nodes to discard payload errors before transmitting data on the network.
C. It allows receivers to correct errors upon data arrival.
D. It allows deep inspection of data payload fields.
Answer: C
QUESTION 200
Which two routing protocols support Cisco MPLS TE Tunnels? (Choose two.)
A. IS-IS
B. RIP
C. BGP
D. OSPF
E. EIGRP
Answer: AD
QUESTION 201
Which protocol is used for communication between the PCE and PCC?
A. ICMP
B. PCEP
C. CEF
D. POP
Answer: B
Resources From:
1.2022 Latest Braindump2go 350-501 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-501.html
2.2022 Latest Braindump2go 350-501 PDF and 350-501 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1DRhL9-RXciswyuF0Mtum6o8JlQET1RiO?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!